|
Getting your Trinity Audio player ready...
|
What is the Internet of Things (IoT)?
The Internet of Things (IoT) refers to a vast network of connected devices, each possessing a unique identifier. These devices automatically collect and exchange data over a network.
Applications of IoT
IoT devices find their use across various sectors and industries:
- Consumer Applications: IoT consumer products include smartphones, smartwatches, and smart home devices. These allow users to control everything, from air conditioning to door locks, all through a single interface.
- Business Applications: In the business realm, companies utilize a range of IoT devices, such as smart security cameras, vehicle trackers, and sensors that gather data on industrial machinery. Moreover, these devices enhance operational efficiency and enable real-time decision-making.
- Governmental Applications: Governments deploy IoT devices for various purposes, including tracking wildlife, monitoring traffic congestion, and issuing alerts during natural disasters. Additionally, these technologies play a crucial role in improving public safety and environmental conservation.”
As IoT becomes an integral part of everyday life, securing these devices is essential yet challenging, given the variety of protocols and vendors involved.
What is IoT Security?
IoT security involves protecting IoT devices and ensuring they do not introduce threats into a network. Given that anything connected to the internet is likely to face attacks at some point, it is, therefore, vital to implement strong security measures. In addition, attackers may attempt to remotely compromise IoT devices through various methods, such as credential theft or exploiting vulnerabilities. Once an attacker gains control, they can, for instance, steal data, conduct Distributed Denial-of-Service (DDoS) attacks, or, consequently, target the rest of the connected network
Unfortunately, many IoT devices are not designed with robust security features. Manufacturers often prioritize usability and market speed over security, making these devices vulnerable to attacks.
Important Threats to IoT Devices
1. Firmware Vulnerability
Firmware is a type of software that runs directly over the hardware. In PCs and phones, the firmware is known as the operating system (e.g., Windows, Android), which addresses most security issues. Conversely, IoT firmware is typically custom-made and maintained in-house; therefore, this necessitates companies to secure it themselves.
“Most IoT firmware lacks robust security protections, such as firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS). Furthermore, many firmware versions have known vulnerabilities that, unfortunately, cannot be patched.These may stem from third-party libraries, modules, device drivers, or even security flaws within the firmware itself. Consequently, IoT devices are often open to attacks targeting these vulnerabilities.
Malware may exploit firmware vulnerabilities by embedding its code within the firmware. Without cryptographic signatures to detect intrusions, the malware remains hidden, making it challenging to identify and eliminate.
Effects of Exploitation:
- Spying on user activities
- Exfiltrating essential user data
- Remote control of the system
- Denial of service
Mitigations for Firmware Vulnerabilities:
- Constant identification and monitoring of firmware vulnerabilities
- Regular firmware updates
- Implementation of secure booting processes
- Continuous verification of firmware to ensure it is uncompromised
2. Authentication Vulnerabilities
IoT devices often communicate data to nearby devices or the cloud using the internet or low-frequency protocols. If these communications are weakly authenticated, attackers can easily compromise them. The nature of authentication methods can vary based on the protocol used.
For example:
- Controllers: Weak authentication might involve simple usernames or passwords for SSH or open APIs for communication between the controller and the server.
- BLE Devices: Weak authentication can occur when using easily decryptable AES keys.
Effects of Exploitation:
- Eavesdropping on user communications
- Remote control of systems through Man-in-the-Middle (MITM) attacks
- Unauthorized access to user data
Mitigations for Authentication Vulnerabilities:
- Always implement strong authentication methods and avoid using default credentials.
OWASP Top 10 Vulnerabilities in IoT
- Weak, Guessable, or Hard-Coded Passwords: These vulnerabilities allow unauthorized access, leading to data theft and system control.
- Insecure Network Services: Exposed network services may leak critical information to public networks.
- Insecure Ecosystem Interfaces: Third-party software, hardware, and services create risks for the entire ecosystem.
- Lack of Secure Update Mechanism: Failing to maintain secure software can leave devices vulnerable to takeover and data exfiltration.
- Use of Insecure or Outdated Components: This can lead to unauthorized access and the formation of botnets for DDoS attacks.
- Insufficient Privacy Protection: IoT devices often collect more data than smartphones, leading to privacy risks, especially in smart home applications.
- Insecure Data Transfer and Storage: Increased connectivity raises security risks related to data transmission and storage.
- Lack of Device Management: Inadequate management tools can result in poor handling of IoT devices.
- Insecure Default Settings: Many devices ship with weak default configurations, making them easy targets for hackers.
- Lack of Physical Hardening: Physical security measures must be balanced with usability to ensure device effectiveness.
Necessary Steps for IoT Security
- Proactively notify users about devices running outdated software/OS versions.
- Enforce smart password management, including mandatory changes from default credentials.
- Disable remote access unless necessary for core functions.
- Implement strict access control policies for APIs.
- Protect command-and-control (C&C) centers from compromise attempts and DDoS attacks.
Types of IoT Security Testing
- IoT Penetration Testing
- Threat Modeling
- Firmware Analysis
Here mainly we can discuss about importance and ways of Threat modelling
Threat Modelling for IoT
What is Threat Modelling?
Threat modeling is an engineering technique used to identify potential threats, attacks, vulnerabilities, and countermeasures that could affect your application. It helps shape application design, meets security objectives, and reduces risks. The goal is to understand how an attacker might compromise a system and ensure appropriate mitigations are in place.
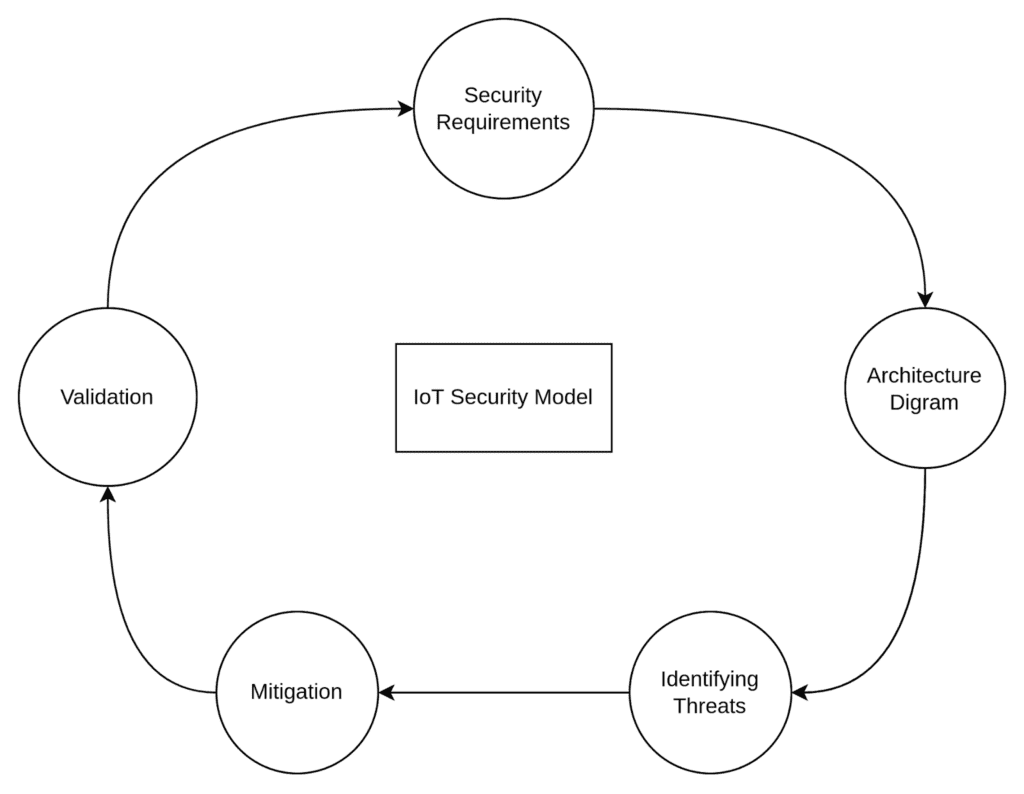
Five Major Threat Modeling Steps:
- Define security requirements based on system architecture.
- Create a comprehensive architecture diagram.
- Identify threats using tools or expertise.
- Mitigate threats based on severity.
- Validate the effectiveness of mitigations.
Threat Models for IoT
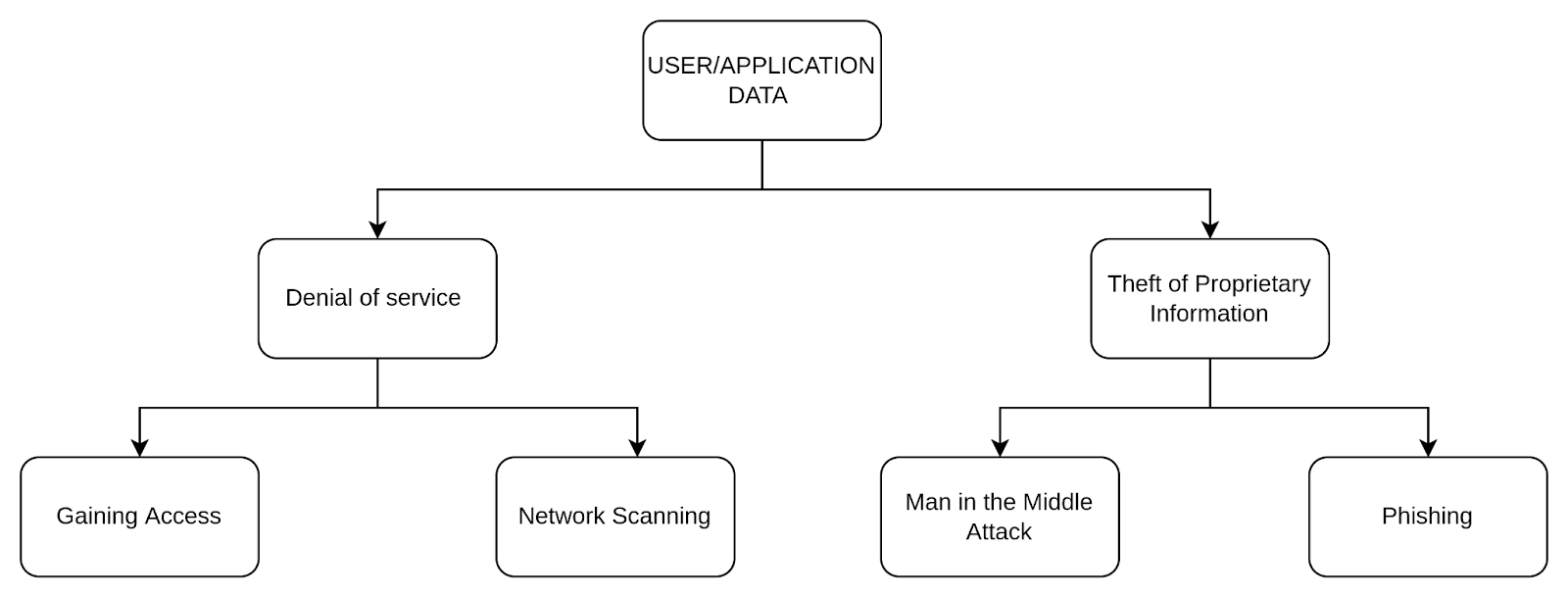
Attack Trees
This classic threat modeling technique uses a tree structure where the main objective is the root, and various methods to achieve that objective are branches.
CIA Triad
The CIA Triad is a fundamental model for securing information, standing for Confidentiality, Integrity, and Availability. Breaching any component of the triad poses serious threats to the system.
- Confidentiality: Ensures that only authorized personnel can access or modify data.
- Integrity: Maintains the trustworthiness of data by preventing improper modifications.
- Availability: Ensures that authorized users can access data whenever required.
STRIDE Model (Mostly Used Model)
STRIDE is a threat modeling framework used to identify and eliminate potential vulnerabilities. It consists of the following categories:
- Spoofing Identity:
- Threat: This category includes any threat related to unintended authentication. In IoT, many devices communicate with each other, making it possible to spoof by mimicking legitimate devices.
- Mitigation: Ensure that access to IoT devices is secure and authenticated. Employ proper authentication mechanisms to avoid unintended communication. Change default usernames and passwords, and use communication protocols that include identity authorization.
- Tampering with Data:
- Threat: This threat occurs if data is manipulated when shared between devices, controllers, and servers.
- Mitigation: Encrypt data shared between IoT controllers, devices, and the cloud. Also, ensure that data stored on IoT devices is encrypted to prevent tampering. The system design should recognize tampered data sent by impersonated devices or servers.
- Repudiation:
- Threat: Repudiation threats arise when a malicious actor performs an illegal operation in a system and denies their involvement. The system lacks the ability to trace malicious activity to identify the hacker.
- Mitigation: Ensure that Syslog and application logs stored in IoT devices are not manipulatable.
- Information Disclosure:
- Threat: This category covers threats that may lead to information leakage.
- Mitigation: Use encryption for data transfer and expose only the required information.
- Denial of Service:
- Threat: This threat can bring the system down and cause denial of service. An excessive load on the system may lead to denial of service, impacting information availability for users.
- Mitigation: Regularly check all services in the system, as one service can cause others to fail. Developers should consider modularity while developing systems so that the impact on one service does not affect others. Additionally, maintaining backups is essential.
- Elevation of Privileges:
- Threat: This threat occurs when one user can access resources outside of their scope. For instance, if an end user can access another user’s data or confidential company data, it impacts the confidentiality of stored information.
- Mitigation: Define the scope of all system users clearly, ensuring developers consider user scope when disclosing any information.
Conclusion
In conclusion, securing IoT devices is paramount in today’s interconnected world. By understanding potential threats and implementing effective security measures, we can protect both users and systems from malicious attacks.

