|
Getting your Trinity Audio player ready...
|
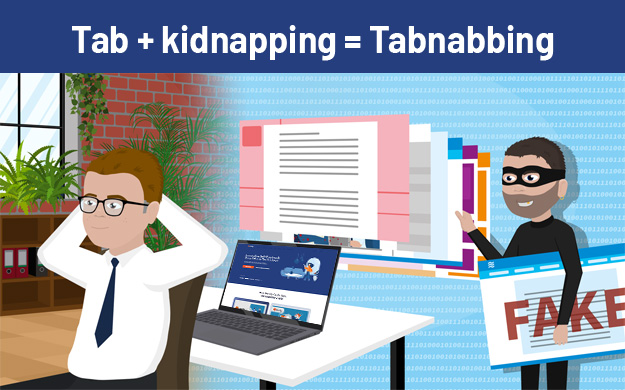
In this blog we gonna see about the Tabnabbing
Cyber attacks have grown from $3 trillion/year in 2015 to $10 trillion/year in 2022. 43% of the attacks are aimed at small businesses and only 14% are prepared to defend. The most common types of cyber attacks on small businesses are:
- Phishing/Social Engineering: 57%
- Compromised/Stolen Devices: 33%
- Credential Theft: 30%
Phishing attack is a method which is used by illegal computer experts to steal data, including login credentials and credit card numbers. An attacker acts as a trusted entity, dupes a victim into opening an email, text or dangerous links. The victim will be tricked to click/download malicious content, that results in stealing of sensitive information of the victim.
Tabnabbing
Social Engineering is a collection of methods used to trick people into performing actions or revealing sensitive information. One of the technology-based-attack is the Tabnabbing attack, coined by Aza Raskin in 2010 as a type of Phishing attack.
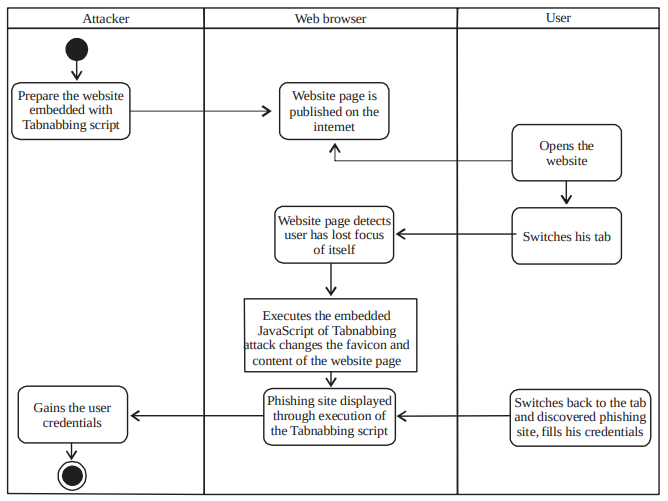
Anatomy of Tabnabbing:
In 2010, aza raskin dubbes an attack that will assist the phishing greatly with a name of tabnabbing which is elaborates as tab+kidnapping.
According to Raskin, an example of successful Tabnabbing attack will start with:
- Victim opened the page of the link and discovered a normal with non-harmful looking page
- The page will detect that it has not been interacted with for a while after being left unattended for a certain moment as victim switch his/her focus to the other tabs
- The page will replace its favicon, title and its contents with the phishing site or malicious script using JavaScript
- Using the page’s favicon and title visible by glancing at the tab, the victim will switch back to the page. There is a probability for the victim not tore-inspect the URL of the page
- If it is a phishing site, the victim will provide his/her credentials as he/she assumes that he/she has been logged out from the site. Otherwise, the malicious content of the page will be triggered and worked as the attacker intended
- After the victim has given the login information and the page has sent it back to the attacker’s server, the victim will be redirected the victim to the original site imitated by the phishing site (Fig. 1)
The attack is typically possible when the source site uses a target instruction in a html link to specify a target loading location that does not replace the current location and then let the current window/tab available and does not include any of the preventative measures. The attack is also possible for links openes via the window.open javascript function.
How to Reproduce?
- Step 1: We require three html files with a code snippet similar to what is provided below:
FileName - attacker.html
--------------------
<!DOCTYPE html>
<html>
<body>
<h1>Attackers Website</h1>
<script>
window.opener.location = "http://127.0.0.1:8000/DupRentlyMain.html";
</script>
</body>
</html>
FileName - DupRentlyMain.html
--------------------
<!DOCTYPE html>
<html>
<body>
<h1> Duplicate Rently Main Website Controlled by Attacker</h1>
</body>
</html>
FileName - RentlyMain.html
--------------------
<!DOCTYPE html>
<html>
<body>
<h1>Rently Main Website</h1>
<a href="http://127.0.0.1:8000/attacker.html" target="_blank" rel="opener">Controlled by the attacker</a>
</body>
</html>- Step 2: Run the below command to run a local web server powered by python
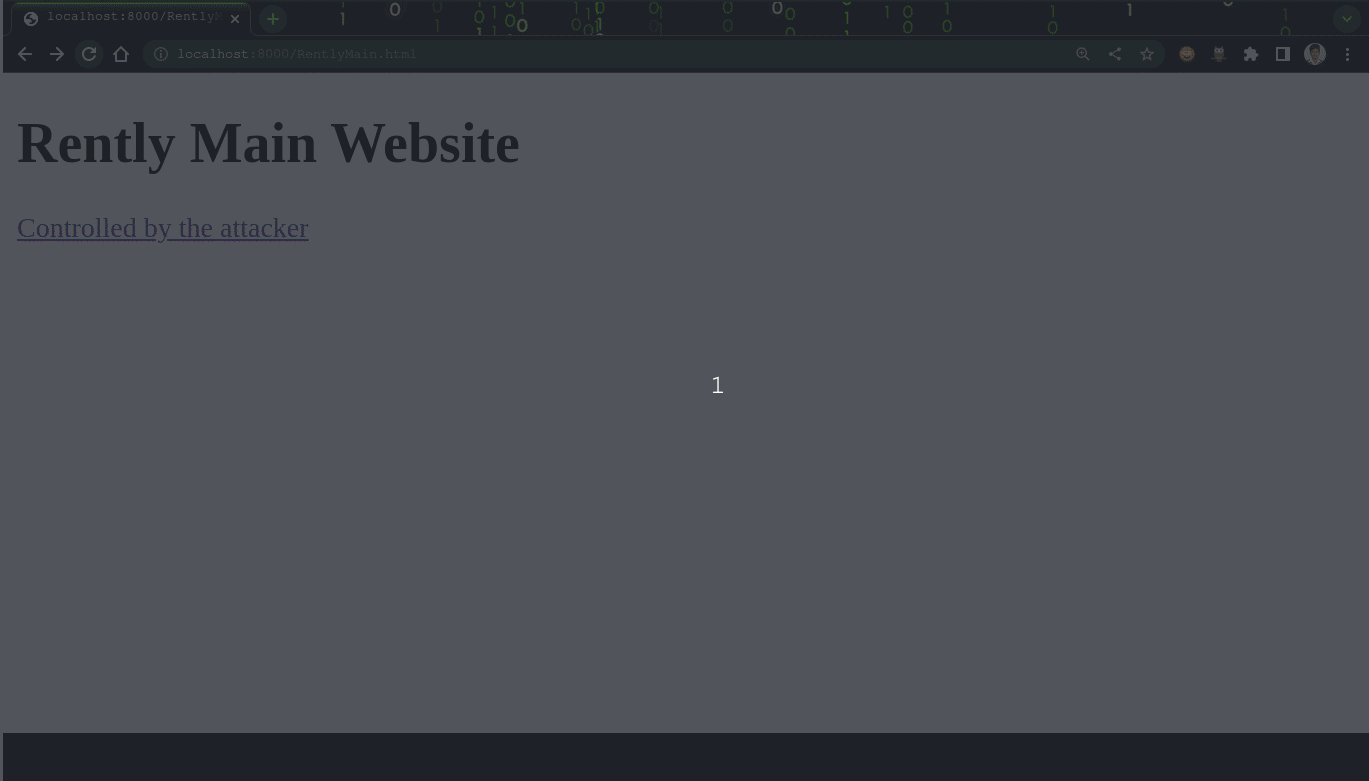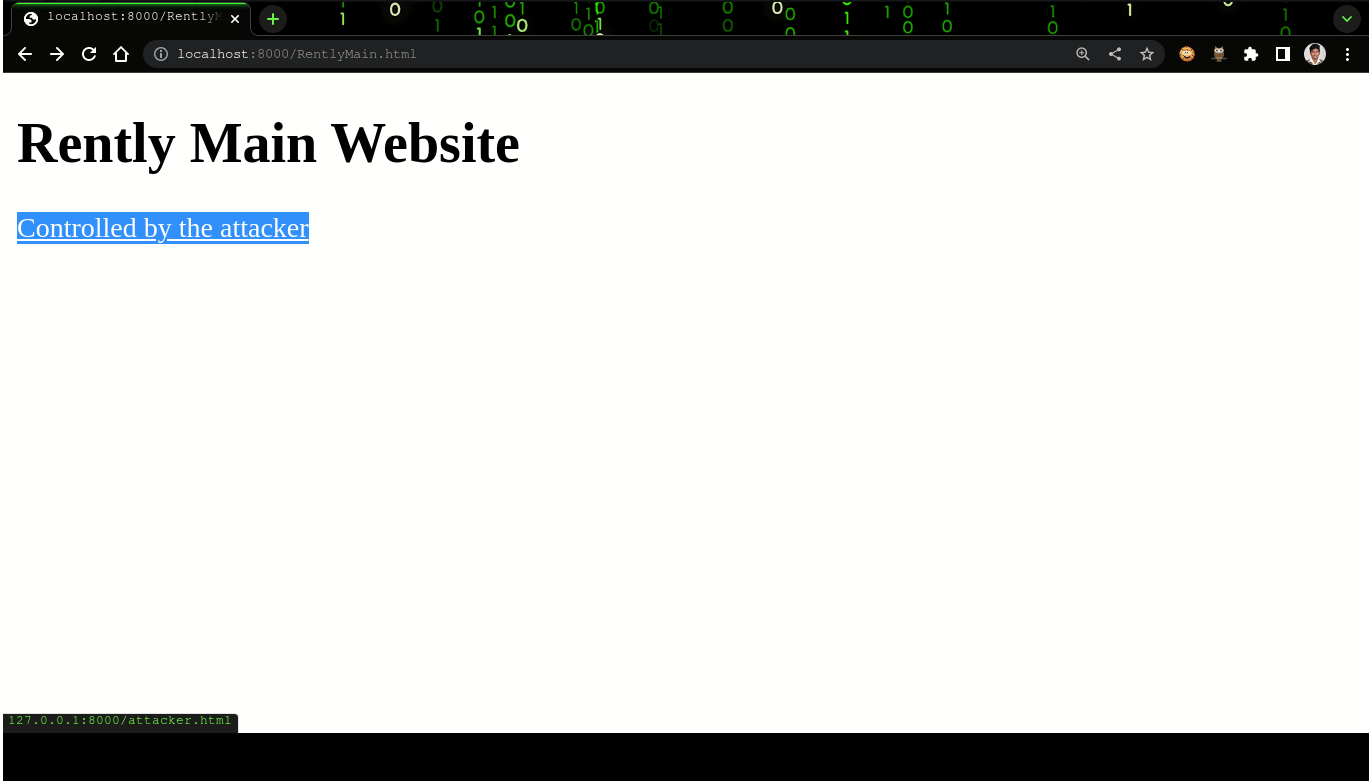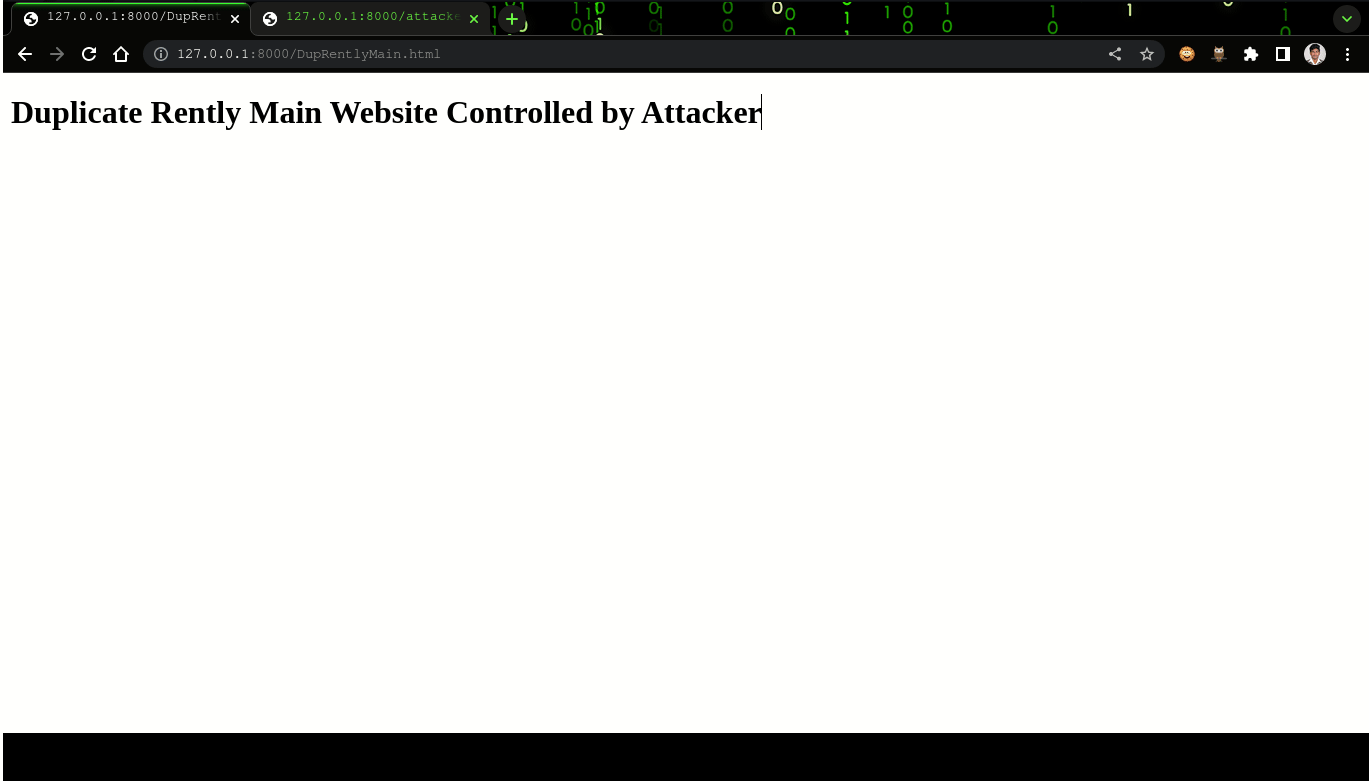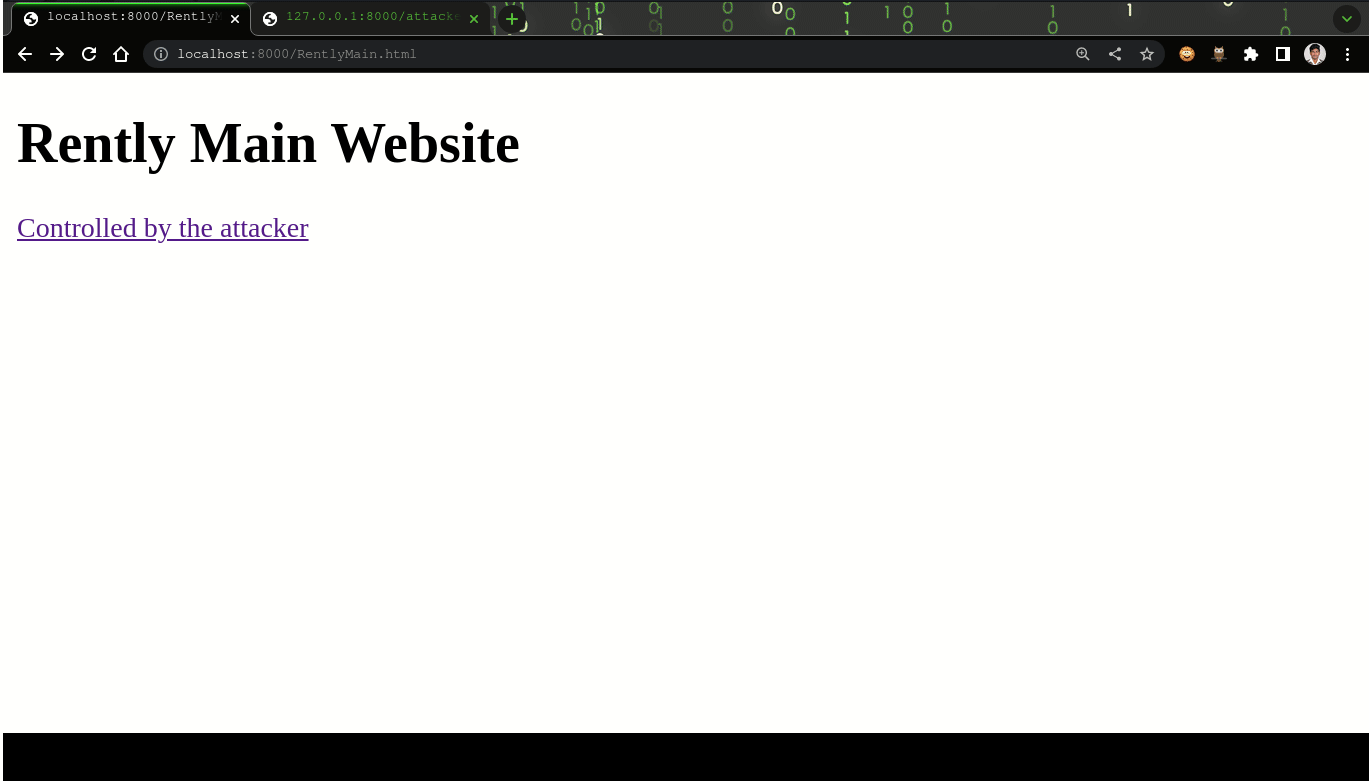
python3 -m http.server- Step 3: Open http://127.0.0.1:8000/RentlyMain.html
- Step 4: Once clicked on the “Controlled by the attacker” link, a new tab opens with the link – http://127.0.0.1:8000/attacker.html
- Step 5: Observe the Original tab change to http://127.0.0.1:8000/DupRentlyMain.html.
Explanation :
- The Original website is http://127.0.0.1:8000/RentlyMain.html and this page uses target=’_blank’ attribute with rel=’opener’ attribute of the anchor tag which link to the attackers site (http://127.0.0.1:8000/attacker.html).
- The attackers site will have a javascript, which will redirect the tab holding the original website to open a new link (http://127.0.0.1:8000/DupRentlyMain.html) which can be a malicious site hosted by the attacker.
- Please refer to Fig. 2 for the Live demo.
How to Test?
Check the HTML files in the application to see if links with target=”_blank” are using the noopener and noreferrer keywords in the rel attribute. If not, it is likely that the application is vulnerable to tabnabbing. Such a link becomes exploitable if it either points to a third-party site. That has been compromises by the attacker, or if it is user-controlles.
Check for places where an attacker can insert links, i.e. control the href argument of an <a> tag. Try to insert a link to a page which has the source code given in the above example, and see if the original domain redirects. We can aslo do this in IE if other browsers don’t work.
How to Prevent?
Tabnabbing is to act on the parent page’s content or location from a newly opened page via the back link exposed by the opener JavaScript object instance. It applies to any HTML link or a JavaScript object window.opener function using the attribute/ instruction target to specify a destination loading location that does not replace the current window/tab available.
We can prevent this by below actions:
- For HTML linker, add attribute rel=”noopener noreferrer” to every link.
- For JavaScript use the below line of code to open a new window.
window.open(url, name, 'noopener,noreferrer,' + windowFeatures);- Add HTTP response header Referrer-Policy: no-referrer to every HTTP response sent by the application.
References:
- https://owasp.org/www-community/attacks/Reverse_Tabnabbing
- https://cheatsheetseries.owasp.org/cheatsheets/HTML5_Security_Cheat_Sheet.html#tabnabbing
- http://docsdrive.com/pdfs/medwelljournals/jeasci/2020/3101-3106.pdf
Get to know about Rently at https://use.rently.com/
To learn more about Engineering topics visit – https://engineering.rently.com
Associate DevSecOps Engineer | Rently

